|
Insup Lee
I am an AI & Security Researcher based in Abu Dhabi, UAE, working on generative models for cybersecurity and drones.
Previously, I spent five years as a researcher at the Agency for Defense Development (ADD), conducting research in AI-driven cybersecurity.
CV / Email / LinkedIn / Google Scholar/ ORCiD |
- 2025.11.30: LeakDiT has been accepted to IEEE Computer Architecture Letters.
- 2025.10.13: Our paper on LLM-based CTI has been accepted to IEEE Access.
- 2025.08.29: Our paper on DDoS detection has been published in JICS.
- 2025.08.12: Our paper on drones has been accepted to IEEE Signal Processing Letters.
- 2025.06.05: MuCamp has been accepted to IEEE Transactions on Information Forensics and Security (TIFS).
- 2025.03.11: I was awarded the UAE ambassador’s commendation for excellence in defense cooperation with the UAE.
- 2024.12.01: Our paper on web shell detection has been published in JKIISC.
- 2024.04.26: I arrived in Abu Dhabi, UAE, where I will be spending one year.
- 2023.09.13: TMR has been accepted to IEEE Access.
- 2023.08.18: BAN has been accepted to IEEE Access.
- 2023.05.26: Camp2Vec has been accepted to ICT Express.
- 2023.03.21: UniQGAN has been accepted to IEEE Transactions on Dependable and Secure Computing (TDSC).
- AI for Cybersecurity: cyber threat intelligence using NLP/LLM, hardware security (side-channel analysis), adversarial ML
- Network and Wireless Security: drones, robust communications, network intrusion detection systems, anomaly detection
- Generative Models: diffusion transformers and GANs for data augmentation, LLM for software vulnerability detection
- Ph.D. Candidate in Cybersecurity, Korea University, Seoul, Republic of Korea, 2019 - Present
- Advisors: Prof. Sangjin Lee and Prof. Seokhie Hong
- B.E. in Cyber Defense, Korea University, Seoul, Republic of Korea, 2014 - 2018
- Studied computer science, cybersecurity, cryptography, and secure coding
- Lecturer, Korea University, Seoul, Republic of Korea, 2025.9 - Present
- Taught graduate-level course "Computer Networks (SCS 302)"
- Research Intern, Indiana University, Bloomington, Indiana, USA, 2025.3 - 2025.6
- Researched quantification methods for ML security in autonomous vehicle systems
- Security Engineer, Ministry of National Defense, Republic of Korea, 2023.8 - 2025.5
- Collaborated with international colleagues and led AI-based security projects in the UAE
- Executed cyber defense operations and developed automation tools at the Cyber Operations Command
- Researcher, Agency for Defense Development (ADD), Seoul, Republic of Korea, 2018.7 - 2023.7
-
Conducted AI-based security research and in-house software development (Advisor: Prof. Changhee Choi)
(1) "Detection of Nation-Sponsored Cyber Attacks Using NLP Technologies" (Apr 2021 - Jul 2023)
(2) "Generative Models for Cybersecurity Data Augmentation" (Jun 2019 - Oct 2020)
(3) "IPADS: Integrated Proactive and Adaptive Defense Systems" (Aug 2018 - May 2019) - Published seven international papers, four patents, and 12 domestic papers
(J: journal / C: conference / P: patent)
Under Review
-
(Blind Review)
Daehyeon Bae, Sujin Park, Insup Lee, Young-Giu Jung, Kyeongsik Lee, Heeseok Kim, Seokhie Hong -
(Blind Review)
Sujin Park, Daehyeon Bae, Insup Lee, Jeonghyeok Kim, Haengrok Oh, Heeseok Kim, Seokhie Hong
|
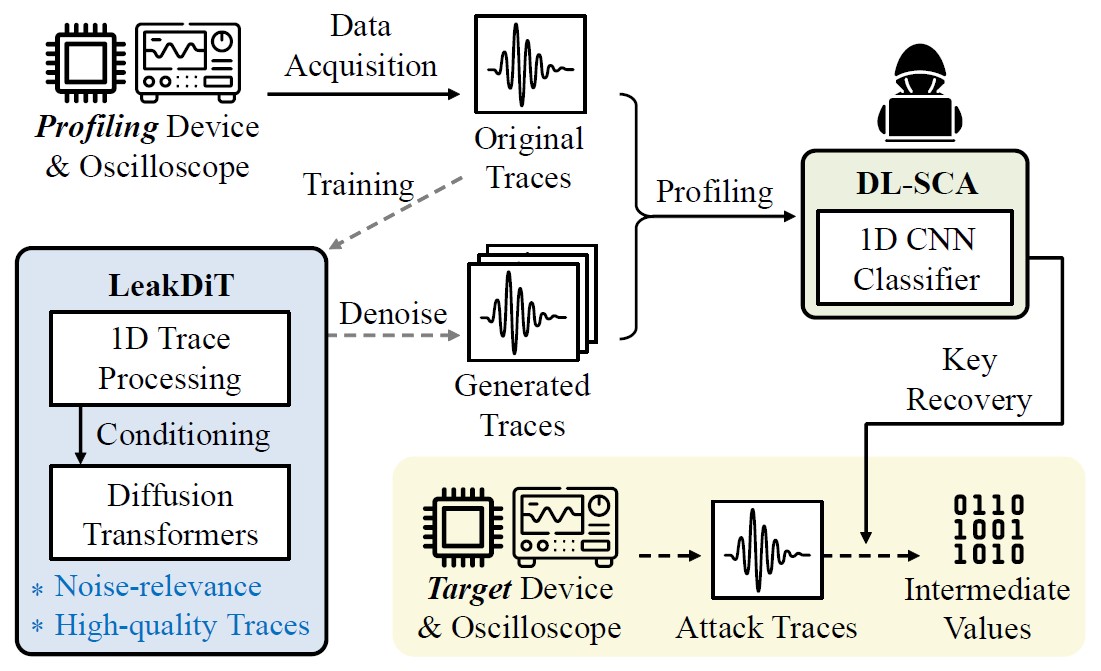
LeakDiT: Diffusion Transformers for Trace-Augmented Side-Channel Analysis
Insup Lee, Daehyeon Bae, Seokhie Hong, and Sangjin Lee IEEE Computer Architecture Letters 2025 [Paper] (SCI 2024 Top 79.2% in Computer Science, Hardware & Architecture) |
|
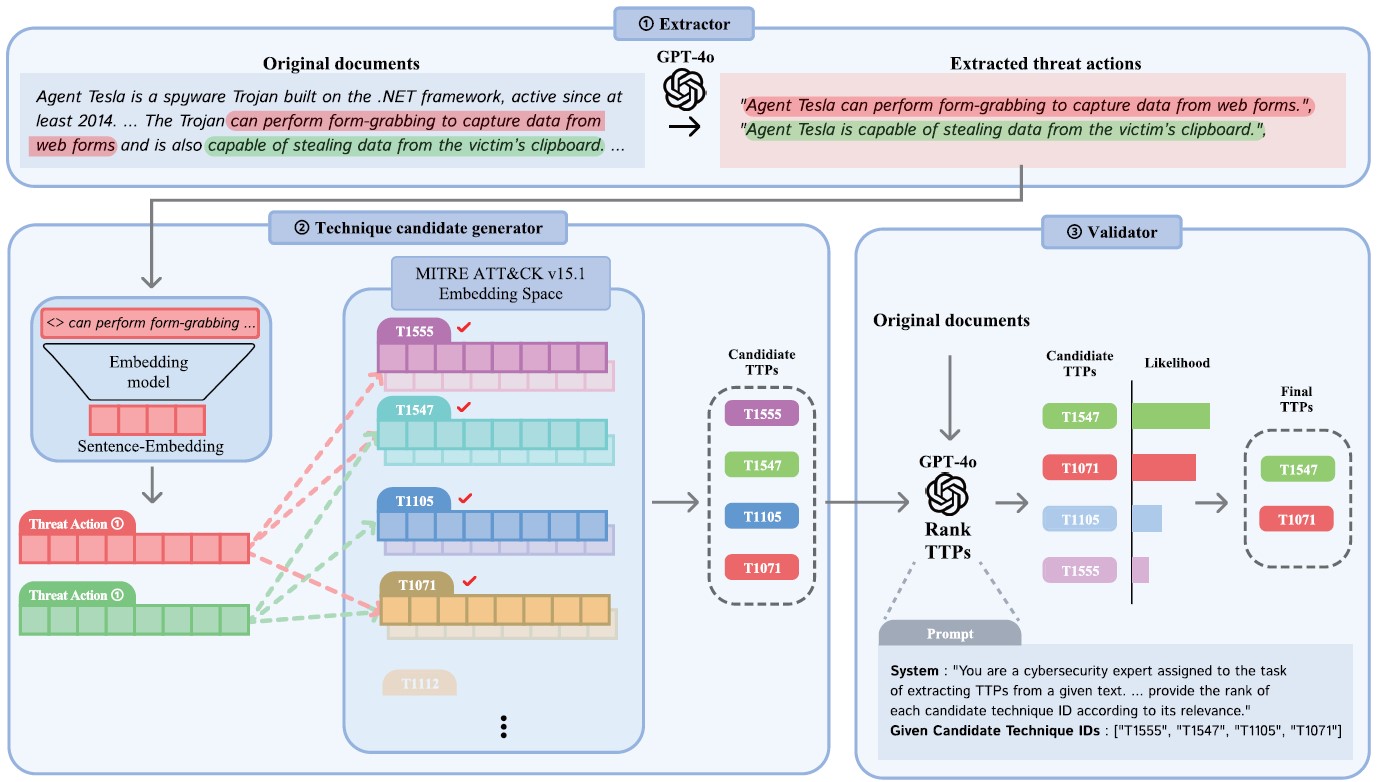
Multi-Step LLM Pipeline for Enhancing TTP Extraction in Cyber Threat Intelligence
Hyoungrok Kim, Donghyeon Lee, Insup Lee, Soohan Lee, and Sangjin Lee IEEE Access 2025 [Paper] (SCI 2024 Top 34.8% in Engineering, Electrical & Electronic) |
|
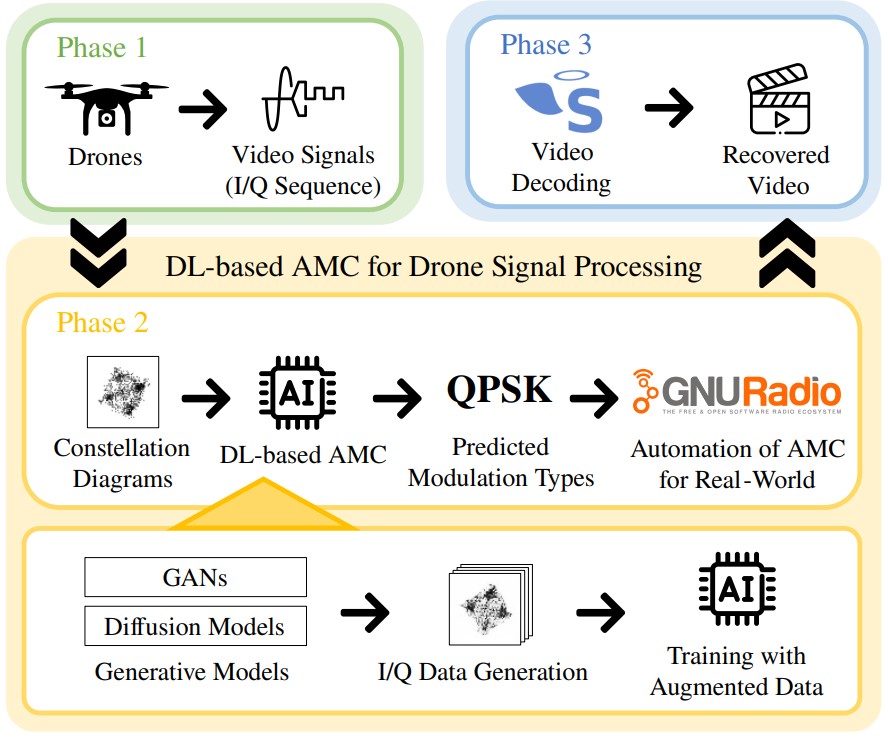
Enhancing Modulation Classification via Diffusion Transformers for Drone Video Signal Processing
Insup Lee, Khalifa Alteneiji, and Mohammed Alghfeli IEEE Signal Processing Letters 2025 [Paper] (SCI 2024 Top 31.6% in Engineering, Electrical & Electronic) |
|
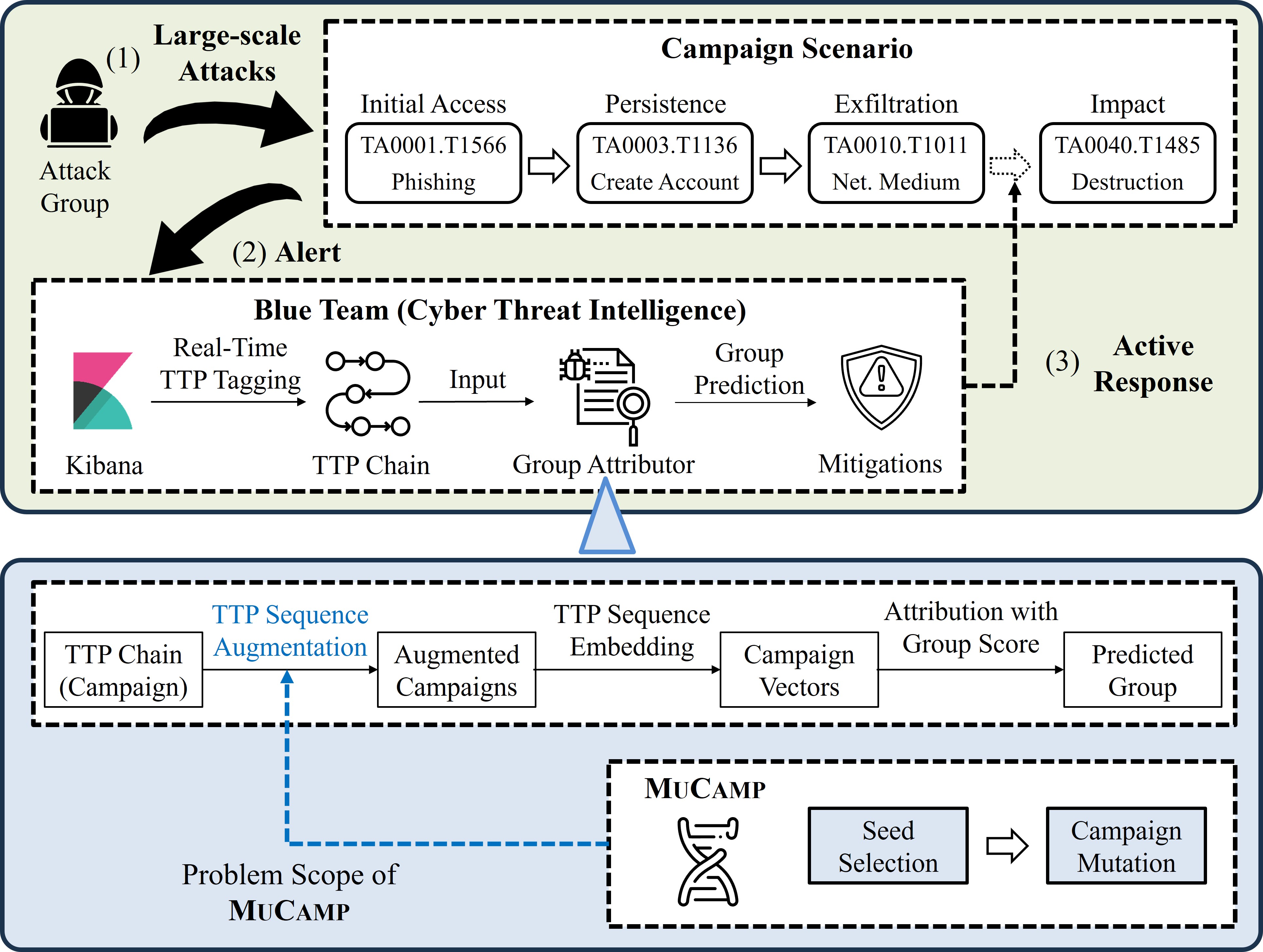
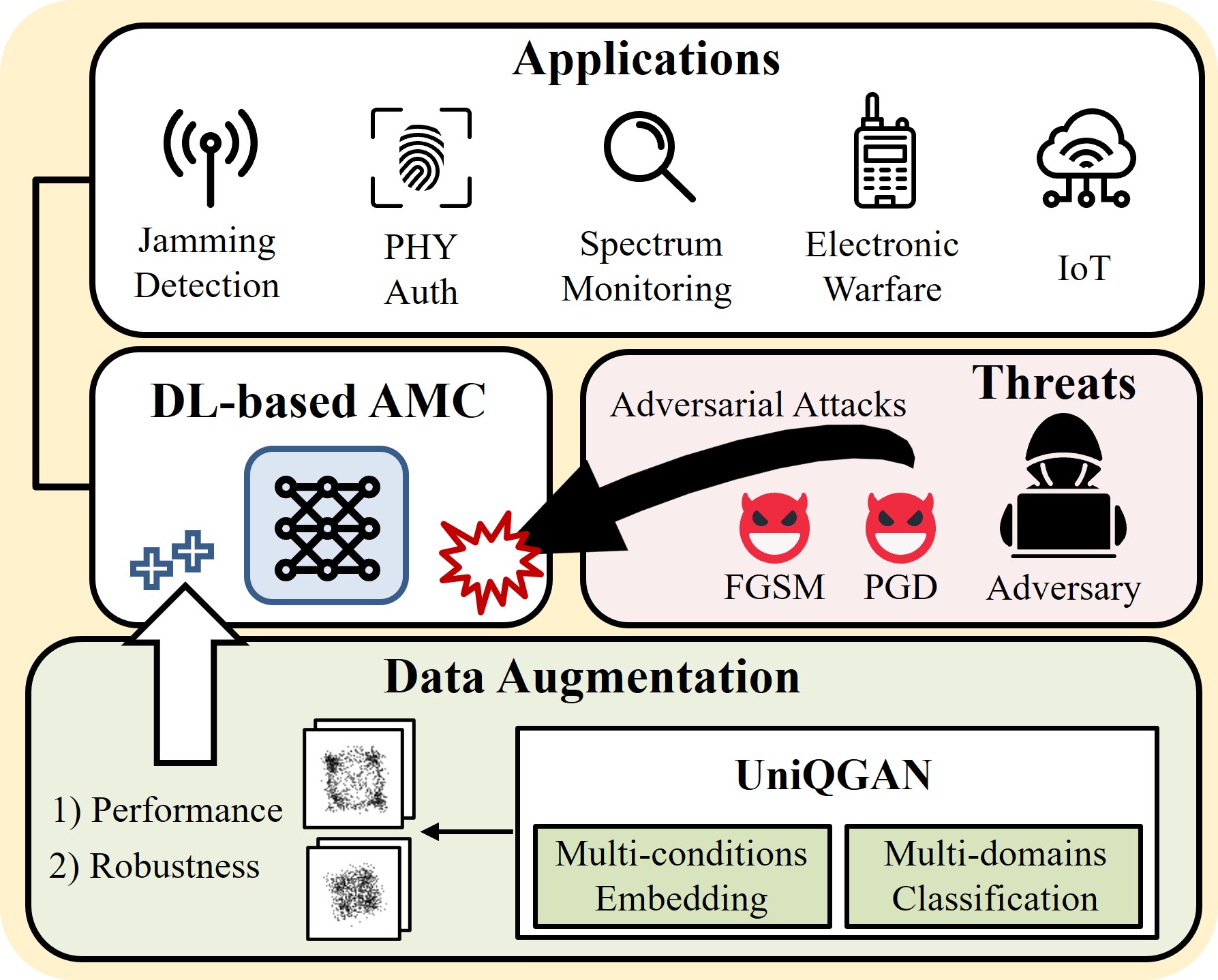
MuCamp: Generating Cyber Campaign Variants via TTP Synonym Replacement for Group Attribution
Insup Lee and Changhee Choi IEEE Transactions on Information Forensics and Security (TIFS) 2025 [Paper] (SCI 2024 I/F Top 7.8% in Computer Science, Theory & Methods) |
|
UniQGAN: Towards Improved Modulation Classification With Adversarial Robustness Using Scalable Generator Design
Insup Lee and Wonjun Lee IEEE Transactions on Dependable and Secure Computing (TDSC) 2024 [Paper] (SCI 2023 I/F Top 4.9% in Computer Science, Software Engineering) |
|
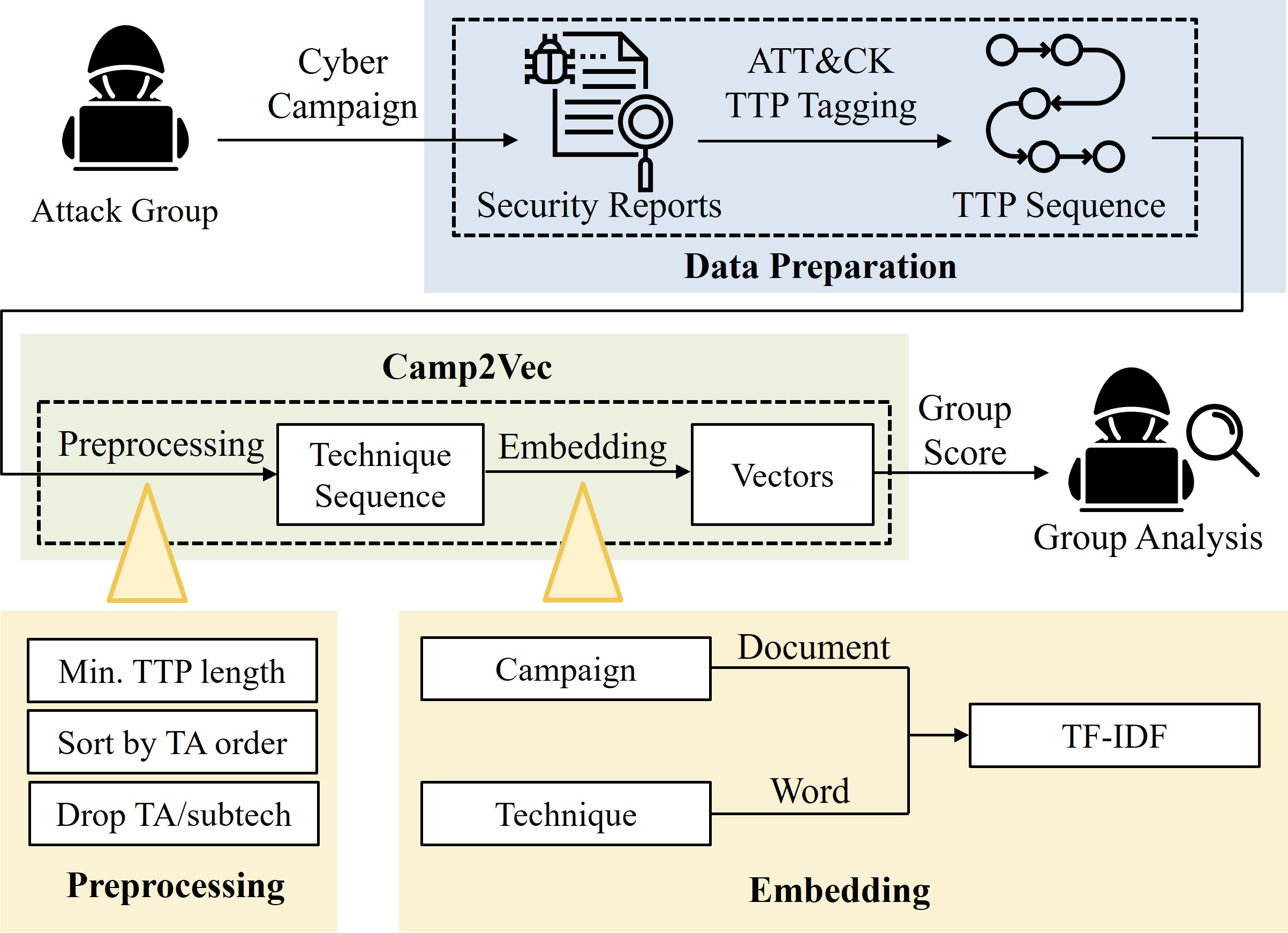
Camp2Vec: Embedding Cyber Campaign With ATT&CK Framework for Attack Group Analysis
Insup Lee and Changhee Choi ICT Express 2023 [Paper] (SCI 2023 Top 23.0% in Computer Science, Information Systems) |
|
|
Exploiting TTP Co-occurence via GloVe-Based Embedding With ATT&CK Framework
Chanho Shin, Insup Lee, and Changhee Choi IEEE Access 2023 [Paper] (SCI 2023 Top 34.4% in Engineering, Electrical & Electronic) |
|
|
BAN: Predicting APT Attack Based on Bayesian Network With MITRE ATT&CK Framework
Youngjun Kim, Insup Lee, Hyuk Kwon, Gyeongsik Lee, and Jiwon Yoon IEEE Access 2023 [Paper] (SCI 2023 Top 34.4% in Engineering, Electrical & Electronic) |
|
|
UniQGAN: Unified Generative Adversarial Networks for Augmented Modulation Classification
Insup Lee and Wonjun Lee IEEE Communications Letters 2022 [Paper] (SCI 2023 Top 33.2% in Telecommunications) |
|
|
Encrypted Malware Traffic Detection Using Incremental Learning
Insup Lee, Heejun Roh, and Wonjun Lee IEEE INFOCOM - Poster Session 2020 [Paper] |
|
|
Anomaly Dataset Augmentation Using Sequence Generative Models
Sunguk Shin, Insup Lee, and Changhee Choi IEEE International Conference on Machine Learning and Applications (ICMLA) 2019 [Paper] |
|
|
Opcode Sequence Amplifier Using Sequence Generative Adversarial Networks
Changhee Choi, Sunguk Shin, and Insup Lee International Conference on ICT Convergence (ICTC) 2019 [Paper] |
-
Method for Augmentating Cyber Attack Campaign Data to Identify Attack Group, and Security System Performing Same
Changhee Choi and Insup Lee
Korea Patent Application Number. 10-2024-0176082, December 2, 2024. -
Information Identification Method and Electronic Apparatus Thereof
Changhee Cho, Insup Lee, Chanho Shin, and Sungho Lee
Korea Patent Application Number. 10-2024-0006106, January 15, 2024. -
Method for Training Attack Prediction Model and Device Therefor
Changhee Choi, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Insup Lee
U.S. Patent Number. US20230308462A1, September 28, 2023. -
Appratus, Method, Computer-readable Storage Medium and Computer Program for Generating Operation Code
Changhee Choi, Sunguk Shin, and Insup Lee
Korea Patent Number. 10-2246797, April 30, 2021.
- Sujin Park, Daehyeon Bae, Insup Lee, Heeseok Kim, and Seokhie Hong, “EM-Based Anomaly Detection using a Dual-Domain Approach,” in Proc. of the KIISC Winter Conference (CISC-W), Nov. 2025. (Selected as an Outstanding Paper Award)
- Jebin Kim, Insup Lee, Chanho Jeon, Suhri Kim, Seokhie Hong, and Sangjin Lee, “Reinforcement Learning for Parameter Optimization in CADO-NFS Polynomial Selection,” in Proc. of the KIISC Winter Conference (CISC-W), Nov. 2025.
- Sujin Park, Daehyeon Bae, Insup Lee, Heeseok Kim, and Seokhie Hong, “A Statistical Time-Domain Approach to Anomaly Detection for Robotic-Arm MCU,” in Proc. of the KIMST Fall Conference, Nov. 2025.
- Hyunjun Park and Insup Lee, “Enhanced DDoS Detection via Traffic Volume-Based Labeling and Transfer Learning,” Journal of Internet Computing and Services (JICS), vol. 26, no. 4, pp. 1-8, Aug. 2025.
- Kangmun Kim and Insup Lee, “User Behavior Embedding via TF-IDF-BVC for Web Shell Detection,” Journal of The Korea Institute of Information Security & Cryptology (JKIISC), vol. 34, no. 6, pp. 1231-1238, Dec. 2024.
- Insup Lee, Chanho Shin, and Changhee Choi, “Mutating Cyber Camapaign With TTP Word Replacement,” in Proc. of the KIMST Annual Conference, Jun. 2023.
- Chanho Shin, Insup Lee, and Changhee Choi, “Towards GloVe-Based TTP Embedding With ATT&CK Framework,” in Proc. of the KIMST Annual Conference, Jun. 2023.
- Changhee Choi, Insup Lee, Chanho Shin, and Sungho Lee, “Cyber Threat Campaign Analysis Based on PEGASUS and RoBERTa Model,” in Proc. of the KIMST Annual Conference, Jun. 2023.
- Insup Lee, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Changhee Choi, “Analyzing Cyberattack Campaign Similarity via TTP Sequence Embedding,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Sunguk Shin, Insup Lee, Chanho Shin, Seongyeon Seo, and Changhee Choi, “Cyber Campaign Analysis With TTP Embedding Using TF-IDF,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Chanho Shin, Sunguk Shin, Insup Lee, Seongyeon Seo, and Changhee Choi, “Classifying TTP Based on CIA Labeling,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Changhee Choi, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Insup Lee, “Cyber Attack Group Classification Using Siamese LSTM,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Chanho Shin, Sunguk Shin, Seongyeon Seo, Insup Lee, and Changhee Choi, “Embedding and Training RNN to Estimating the Goal of Cyber Attack,” in Proc. of the KIMST Fall Conference, Nov. 2021.
- Sunguk Shin, Chanho Shin, Seongyeon Seo, Insup Lee, and Changhee Choi, “The Proposed Approach for Country Prediction With TTP-based Cyber Data Using GCN,” in Proc. of the KIMST Fall Conference, Nov. 2021.
- Changhee Choi, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Insup Lee, “Deep Learning for Estimating Next Action of Cyber Attack,” in Proc. of the KIMST Fall Conference, Nov. 2021.
- Yongbin Park, Sunguk Shin, and Insup Lee, “A Study on Evaluation Method of NIDS Datasets in Closed Military Network,” Journal of Internet Computing and Services (JICS), vol. 21, no. 2, pp. 121-130, Apr. 2020.
- Insup Lee, Jingook Kim, and Jeongchan Park, “Analysis of Weight Setting in Incremental Learning to Improve Real-Time Intrusion Detection,” in Proc. of the KIMST Annual Conference, Jun. 2019.
-
Outstanding Paper Award, CISC-W'25, KIISC, November 2025
(Paper TItle: EM-Based Anomaly Detection using a Dual-Domain Approach) -
Ambassador’s Commendation for excellence in defense cooperation, March 2025
Embassy of the Republic of Korea to the United Arab Emirates -
The 3rd Prize, Military Cybersecurity Experts Hackathon (Cyber Talpiot), December 2023
Ministry of Science and ICT, Republic of Korea -
Full Tuition Scholarship (Korea University), 2014 - 2018
Ministry of National Defense, Republic of Korea
- AI Cyber Challenge (AIxCC), DARPA and ARPA-H, USA, 2024.4 - 2024.8
- Participated in the semifinal round as a member of Team KORIA, submitting our cyber reasoning system that leverages LLMs for automated detection and patching of software vulnerabilities
- SW Outsourcing Development, KCMVP-Certified Cryptographic Module, 2017.6 - 2018.3
- Implemented a cryptographic module with 25,000 LoC in C while following secure coding conventions
- Covered the ARIA block cipher (modes: ECB, CBC, CTR), hash functions (SHA-256, SHA-512), and HMAC-based DRBG for Windows (.dll) and Linux (.so), respectively
- Frameworks/Tools: PyTorch, Keras, TensorFlow, scikit-learn, pandas, Git, Streamlit
- Programming Languages: Python, C, JavaScript, SQL
- Languages: English, Korean
- Reviewer, IEEE Transaction on Dependable and Secure Computing (TDSC), 2025
- Reviewer, IEEE Transaction on Communications (TCOM), 2025
- Reviewer, IEEE Journal on Selected Areas in Communications (JSAC), 2025
- Reviewer, IEEE International Conference on Computer Communications (INFOCOM), 2023-2024
- Reviewer, IEEE Communications Letters, 2022
- Lecturer, Fall 2025: Computer Networks (SCS302), Korea University
Last Update: November 2025
