|
Insup Lee
Hi! I am a captain of ROK Army, currently working in Abu Dhabi, UAE.
Prior to this, I completed five years of AI-based cybersecurity research at the Agency for Defense Development (ADD).
I am in my last year of a seven-year mandatory military service, which will conclude in May 2025.
Email / LinkedIn / Google Scholar / ORCiD |
- 2024.04.08: I joined Ministry of National Defense, Abu Dhabi, UAE.
- 2024.02.24: I successfully finished the preliminary proposal for Ph.D. dissertation titled "Generative Models for Scalable and Robust Wireless Networks."
- 2023.12.10: I won the 3rd prize in Cyber Talpiot Hackathon as a team leader.
- 2023.09.13: TMR has been accepted to IEEE Access.
- 2023.08.18: BAN has been accepted to IEEE Access.
- 2023.08.01: I joined R.O.K. Cyber Operations Command as a cyber officer.
- 2023.05.26: Camp2Vec has been accepted to ICT Express.
- 2023.03.21: UniQGAN has been accepted to IEEE Transactions on Dependable and Secure Computing (TDSC).
- Cybersecurity
- Cyber threat intelligence for large-scale advanced persistent threats
- Network security: (1) robust communications via generative models and (2) machine learning for NIDS
- AI security: robustness and resilience in AI
- Generative Models
- Diffusion models with transformers
- Domain-specific scalability in generative adversarial networks (GAN)
- Adversarial robustness via generative models
- Korea University, Seoul, Republic of Korea (2019 - Present)
- Ph.D. candidate in Cybersecurity, School of Cybersecurity
- Topic: Generative Models for Scalable and Robust Wireless Networks
- Publications: IEEE TDSC'24, IEEE CL'22, IEEE INFOCOM'20-Poster
- Korea University, Seoul, Republic of Korea (2014 - 2018)
- B.Eng. in Dept. of Cyber Defense (CYDF), Division of Information Security
- Ministry of National Defense, Abu Dhabi, UAE (Apr. 2024 - Present)
- Instructor (Army Captain)
- Topic: Education for Cybersecurity
- R.O.K. Cyber Operations Command, Republic of Korea (Aug. 2023 - Apr. 2024)
- Security Engineer (Army Captain)
- Topic: Cyber Operation on Military AI and Network Security
- Agency for Defense Development (ADD), Seoul, Republic of Korea (Jul. 2018 - Jul. 2023)
- Security Researcher, Cyber Technology Center
- Topic: Research on AI-based Cybersecurity and Cyber Threat Intelligence
- Publications: 3 SCI journal papers & 2 international conference papers
- Etc: 5-month Dispatch (Nov. 2020 - Mar. 2021)
Korea University (Sep. 2019 - Present)
Ph.D. Student, advised by Prof. Wonjun Lee
- Generative Models for Scalable and Robust Wireless Networks (May 2020 - Present)
- Keywords: generative models, GAN, adversarial robustness, modulation classification, deep learning
- Frameworks/Tools: PyTorch, IBM ART (Adversarial Robustness Toolbox)
- Publications: [J1], [J5]
- Network Intrusion Detection Systems Using Incremental Learning (Sep. 2019 - Jul. 2020)
- Keywords: network IDS, machine learning, encrypted traffic classification, incremental learning
- Frameworks/Tools: scikit-learn
- Publications: [C3]
Researcher, advised by Dr. Changhee Choi
- Detecting State-Sponsored Cyberattacks via Machine Learning (Apr. 2021 - Jul. 2023)
- Keywords: CTI, data augmentation, embedding, NLP, cyber campaign, SOAR, MITRE ATT&CK, TTPs
- Frameworks/Tools: PyTorch, FastAPI, Git, PostgreSQL
- Publications: [J2], [J3], [J4] & one journal paper is submitted (under review)
- Generative Models for Cybersecurity Data Augmentation (Jun. 2019 - Oct. 2020)
- Keywords: generative models, host IDS, sequence data, CycleGAN, SeqGAN, Seq2Seq, ADFA-LD
- Frameworks/Tools: TensorFlow, Node.js, Git
- Publications: [C1], [C2]
- IPADS: Integrated Proactive and Adaptive Defense Systems (Aug. 2018 - May 2019)
- Keywords: anomaly detection, network IDS, in-vehicle network, MilCAN, CIC-IDS2017
- Frameworks/Tools: scikit-learn
(J: journal / C: conference / P: patent)
Under Review
|
|
MuCamp: Generating Cyber Campaign Variants via TTP Synonym Replacement for Group Attribution
Insup Lee and Changhee Choi Submitted to IEEE Transactions on Information Forensics and Security (TIFS) |
|
[J5]
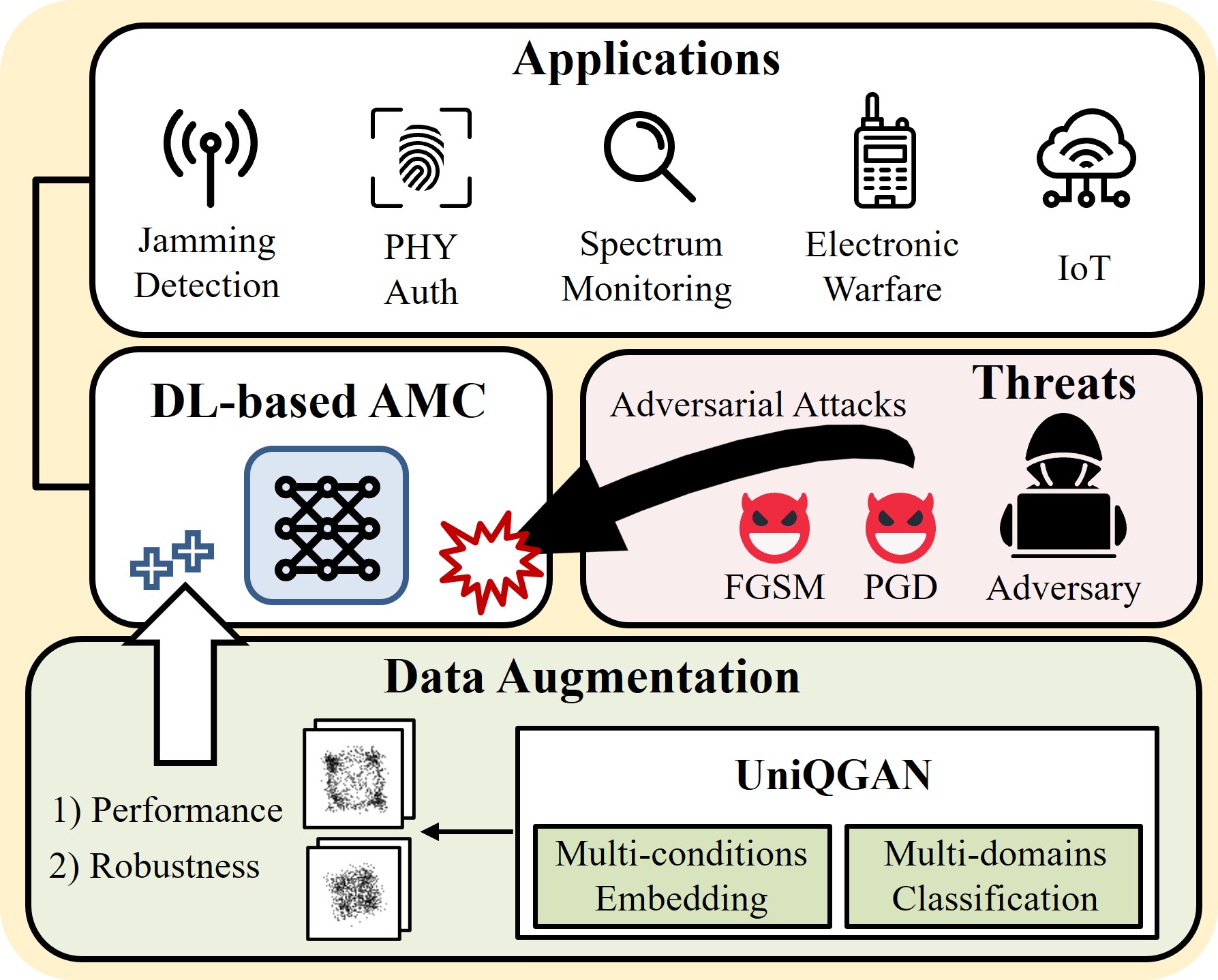
UniQGAN: Towards Improved Modulation Classification With Adversarial Robustness Using Scalable Generator Design
Insup Lee and Wonjun Lee IEEE Transactions on Dependable and Secure Computing (TDSC), 2024 [paper] (SCI 2022 Top 5.56% in Computer Science, Software Engineering) |
|
[J4]
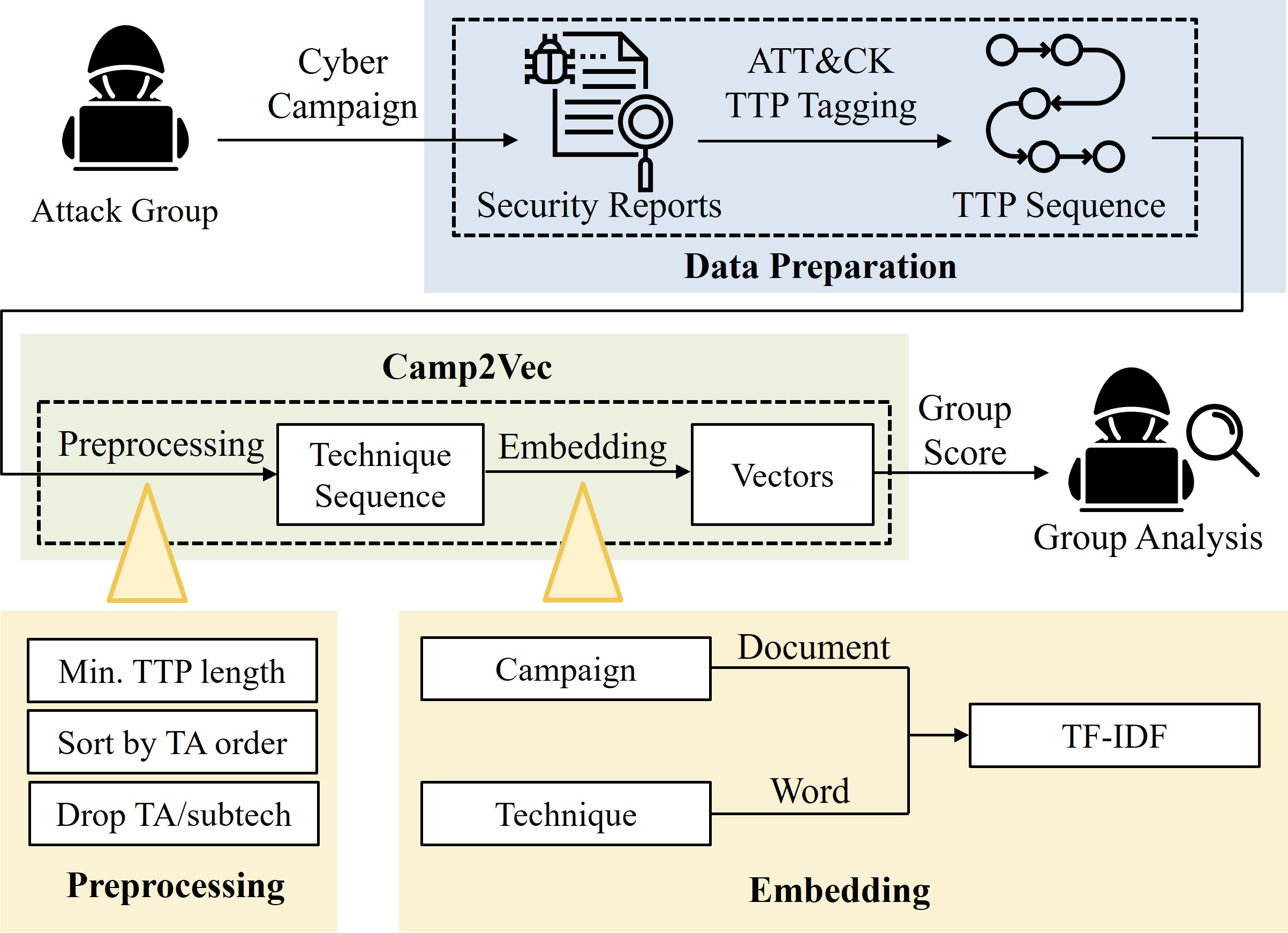
Camp2Vec: Embedding Cyber Campaign With ATT&CK Framework for Attack Group Analysis
Insup Lee and Changhee Choi ICT Express, 2023 (SCI 2022 Top 28.41% in Telecommunications) |
|
|
[J3]
Exploiting TTP Co-occurence via GloVe-Based Embedding With ATT&CK Framework
Chanho Shin, Insup Lee, and Changhee Choi IEEE Access, 2023 (SCI 2022 Top 36.36% in Engineering, Electrical & Electronic) |
|
|
[J2]
BAN: Predicting APT Attack Based on Bayesian Network With MITRE ATT&CK Framework
Youngjun Kim, Insup Lee, Hyuk Kwon, Gyeongsik Lee, and Jiwon Yoon IEEE Access, 2023 (SCI 2022 Top 36.36% in Engineering, Electrical & Electronic) |
|
|
[J1]
UniQGAN: Unified Generative Adversarial Networks for Augmented Modulation Classification
Insup Lee and Wonjun Lee IEEE Communications Letters, 2022 (SCI 2022 Top 43.18% in Telecommunications) |
|
|
[C3]
Encrypted Malware Traffic Detection Using Incremental Learning
Insup Lee, Heejun Roh, and Wonjun Lee IEEE INFOCOM - Poster Session, 2020 |
|
|
[C2]
Anomaly Dataset Augmentation Using Sequence Generative Models
Sunguk Shin, Insup Lee, and Changhee Choi IEEE International Conference on Machine Learning and Applications (ICMLA), 2019 |
|
|
[C1]
Opcode Sequence Amplifier Using Sequence Generative Adversarial Networks
Changhee Choi, Sunguk Shin, and Insup Lee International Conference on ICT Convergence (ICTC), 2019 |
-
[P1]
Method for Training Attack Prediction Model and Device Therefor
Changhee Choi, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Insup Lee
U.S. Patent Application Number. 18/126,005
- Insup Lee, Chanho Shin, and Changhee Choi, “Mutating Cyber Camapaign With TTP Word Replacement,” in Proc. of the KIMST Annual Conference, Jun. 2023.
- Chanho Shin, Insup Lee, and Changhee Choi, “Towards GloVe-Based TTP Embedding With ATT&CK Framework,” in Proc. of the KIMST Annual Conference, Jun. 2023.
- Changhee Choi, Insup Lee, Chanho Shin, and Sungho Lee, “Cyber Threat Campaign Analysis Based on PEGASUS and RoBERTa Model,” in Proc. of the KIMST Annual Conference, Jun. 2023.
- Insup Lee, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Changhee Choi, “Analyzing Cyberattack Campaign Similarity via TTP Sequence Embedding,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Sunguk Shin, Insup Lee, Chanho Shin, Seongyeon Seo, and Changhee Choi, “Cyber Campaign Analysis With TTP Embedding Using TF-IDF,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Chanho Shin, Sunguk Shin, Insup Lee, Seongyeon Seo, and Changhee Choi, “Classifying TTP Based on CIA Labeling,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Changhee Choi, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Insup Lee, “Cyber Attack Group Classification Using Siamese LSTM,” in Proc. of the KIMST Annual Conference, Jun. 2022.
- Chanho Shin, Sunguk Shin, Seongyeon Seo, Insup Lee, and Changhee Choi, “Embedding and Training RNN to Estimating the Goal of Cyber Attack,” in Proc. of the KIMST Fall Conference, Nov. 2021.
- Sunguk Shin, Chanho Shin, Seongyeon Seo, Insup Lee, and Changhee Choi, “The Proposed Approach for Country Prediction With TTP-based Cyber Data Using GCN,” in Proc. of the KIMST Fall Conference, Nov. 2021.
- Changhee Choi, Chanho Shin, Sunguk Shin, Seongyeon Seo, and Insup Lee, “Deep Learning for Estimating Next Action of Cyber Attack,” in Proc. of the KIMST Fall Conference, Nov. 2021.
- Yongbin Park, Sunguk Shin, and Insup Lee, “A Study on Evaluation Method of NIDS Datasets in Closed Military Network,” Journal of Internet Computing and Services (JICS), vol. 21, no. 2, pp. 121-130, Apr. 2020.
- Insup Lee, Jingook Kim, and Jeongchan Park, “Analysis of Weight Setting in Incremental Learning to Improve Real-Time Intrusion Detection,” in Proc. of the KIMST Annual Conference, Jun. 2019.
- Changhee Choi, Sunguk Shin, and Insup Lee, “Appratus, Method, Computer-readable Storage Medium And Computer Program For Generating Operation Code,” Korea Patent Application Number. 10-2019-0141865, November 07, 2019; Korea Patent Number. 10-2246797, April 30, 2021.
- Changhee Choi, Sunguk Shin, and Insup Lee, "Log Extractor For Windows 10 Internet, Event, Process, and Network," Software Registration No. C-2020-035358, October 14, 2020.
-
The 3rd Prize, Military Cybersecurity Experts Hackathon (Cyber Talpiot), Dec. 2023
Ministry of Science and ICT, Republic of Korea -
Full Tuition Scholarship (Korea University), 2014 - 2018
Ministry of National Defense, Republic of Korea
- Reviewer, IEEE International Conference on Computer Communications (INFOCOM), 2022
- Reviewer, IEEE Communications Letters, 2021
- "Towards Intelligent Defense via Federated Learning-Based Military Threat Detection," Military Cybersecurity Experts Seminar (hackathon winners presentation), Dec. 2023
- Research Student, Center for Cyber Resilience Research (C2R2) (Jan. 2022 - Mar. 2023)
- Topic: Research on Cyber Resiliency Measurement and AI Resilience
- SW Outsourcing Development, KCMVP-Certified Cryptographic Module (Jun. 2017 - Mar. 2018)
- Programming Languages: Python, C, JavaScript, SQL, HTML, CSS, PHP
- Frameworks/Tools: PyTorch, TensorFlow, scikit-learn, pandas, Matplotlib, Git, PostgreSQL
Last Update: April 2024